Securely Embrace SaaS Ecosystem
Secure, Manage and Optimize Your SaaS Applications
Securely Embrace SaaS Ecosystem
Secure, Manage and Optimize Your SaaS Applications
Secure, Manage and Optimize Your SaaS Applications
Secure, Manage and Optimize Your SaaS Applications


%
of organizations have faced SaaS incdents
In today’s digital landscape, SaaS platforms are essential yet vulnerable. Frequent breaches involving major providers underscore the urgent need for robust SaaS security. Here’s why it matters.

SaaS platforms are increasingly targeted by cybercriminals, resulting in severe data breaches. Understanding and mitigating these threats is essential for maintaining security.
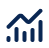
Complex SaaS environments obscure security threats. Achieving full visibility is crucial for identifying and addressing potential vulnerabilities effectively.

Inadequate SaaS security can lead to non-compliance with regulations. Ensuring compliance is vital to avoid penalties and maintain trust.

Weak data governance in SaaS can result in unauthorized access and data loss. Robust data protection measures are necessary to secure sensitive information.
Achieve comprehensive insights into Shadow IT, user behaviour, data exposure, SaaS risks, and compliance.
Enhance your SaaS security by prioritizing and addressing vulnerabilities with AI-driven analytics and automated remediation.
Streamline the management and governance of apps and identities through automation and orchestration, ensuring secure and compliant SaaS usage.
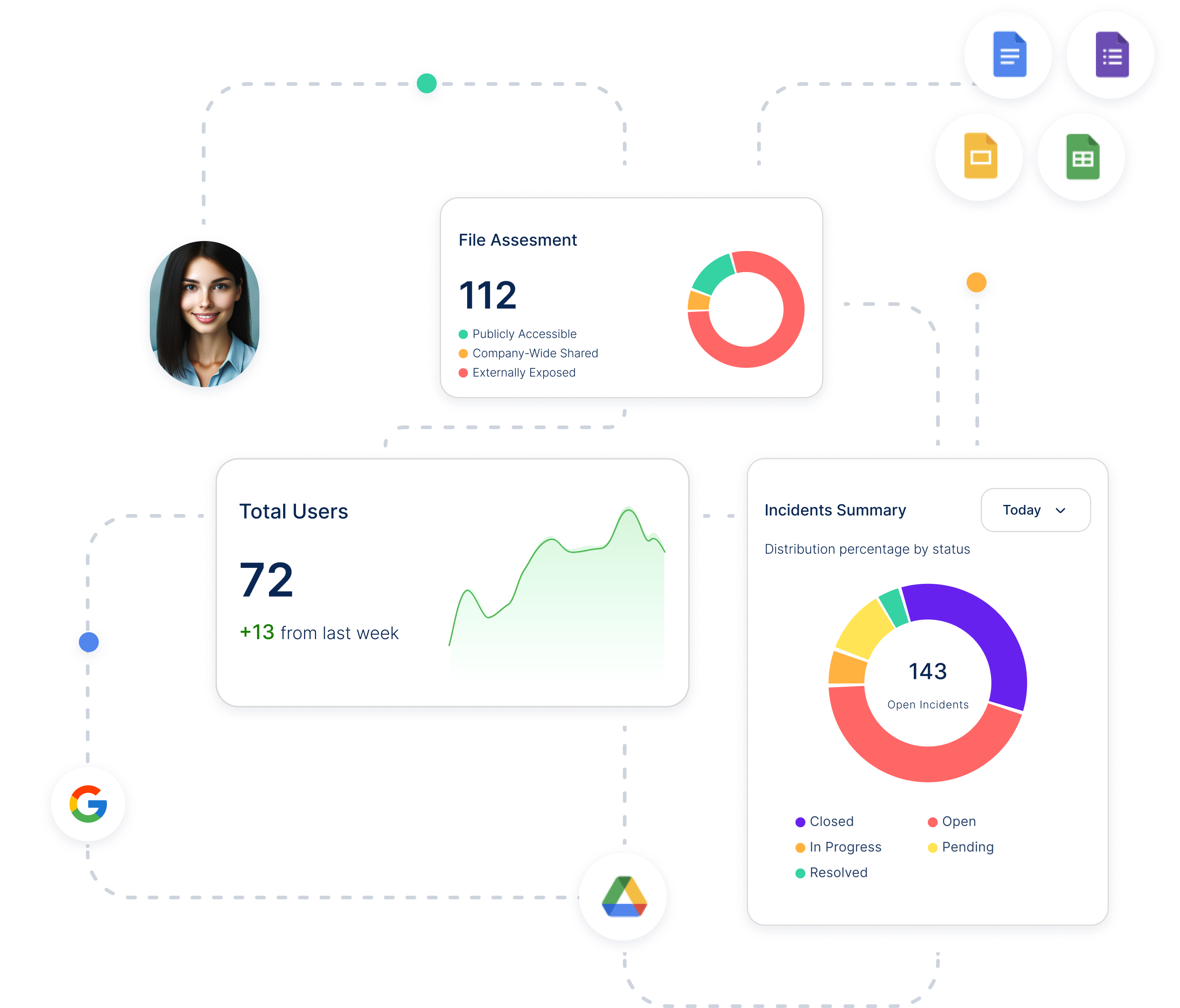

Quick setup and seamless integration with your existing SaaS applications.

Full security posture management for all your SaaS applications.

Security solutions designed to fit the budget of businesses of all sizes.
Unmanaged Saas applications and accounts can lead to security risks ad inefficiencies.
Identify and manage unauthorized SaaS usage to gain complete visibility into your SaaS environment.
Securely offboard users and decommission unfederated SaaS accounts with automated workflows.
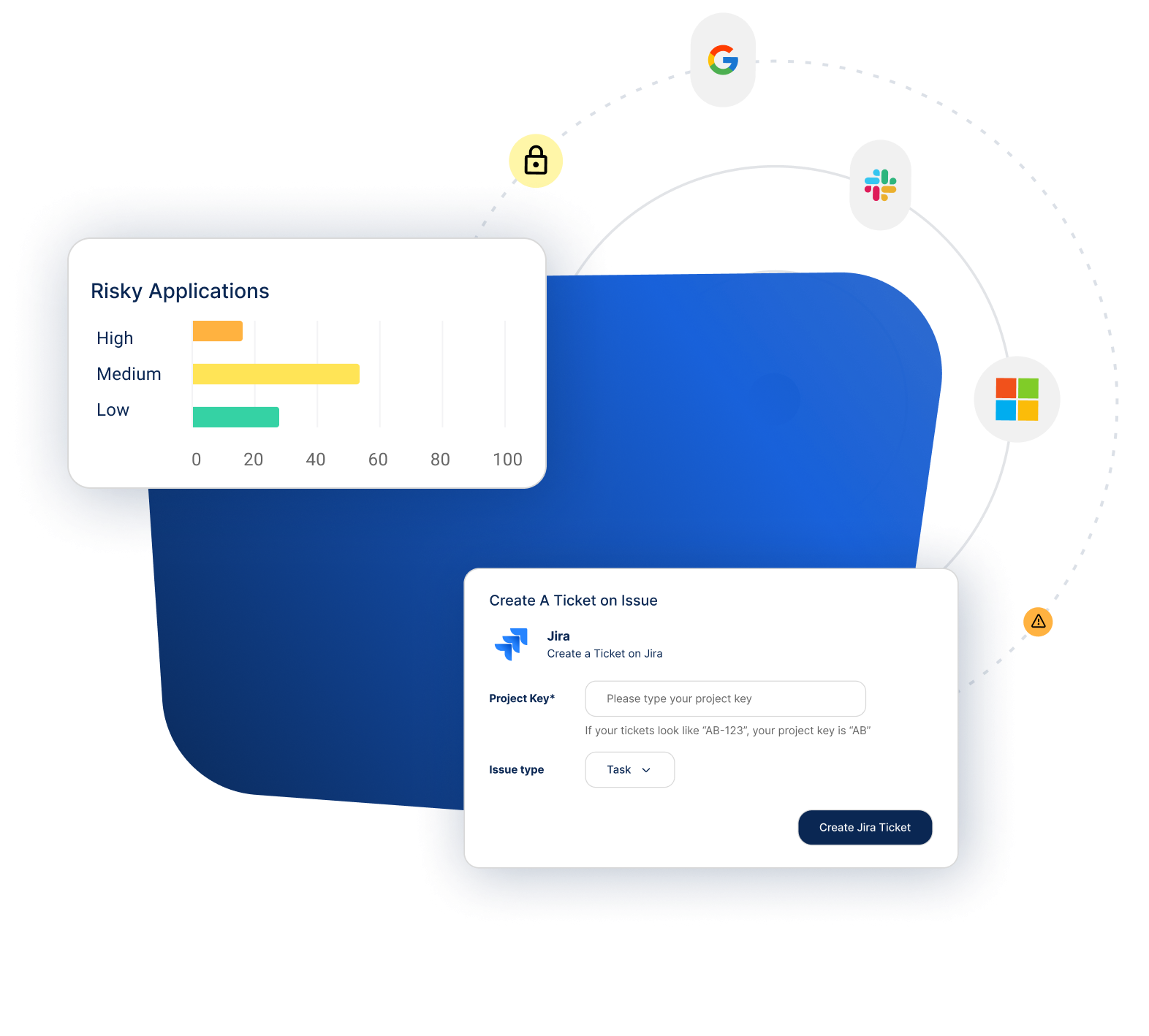
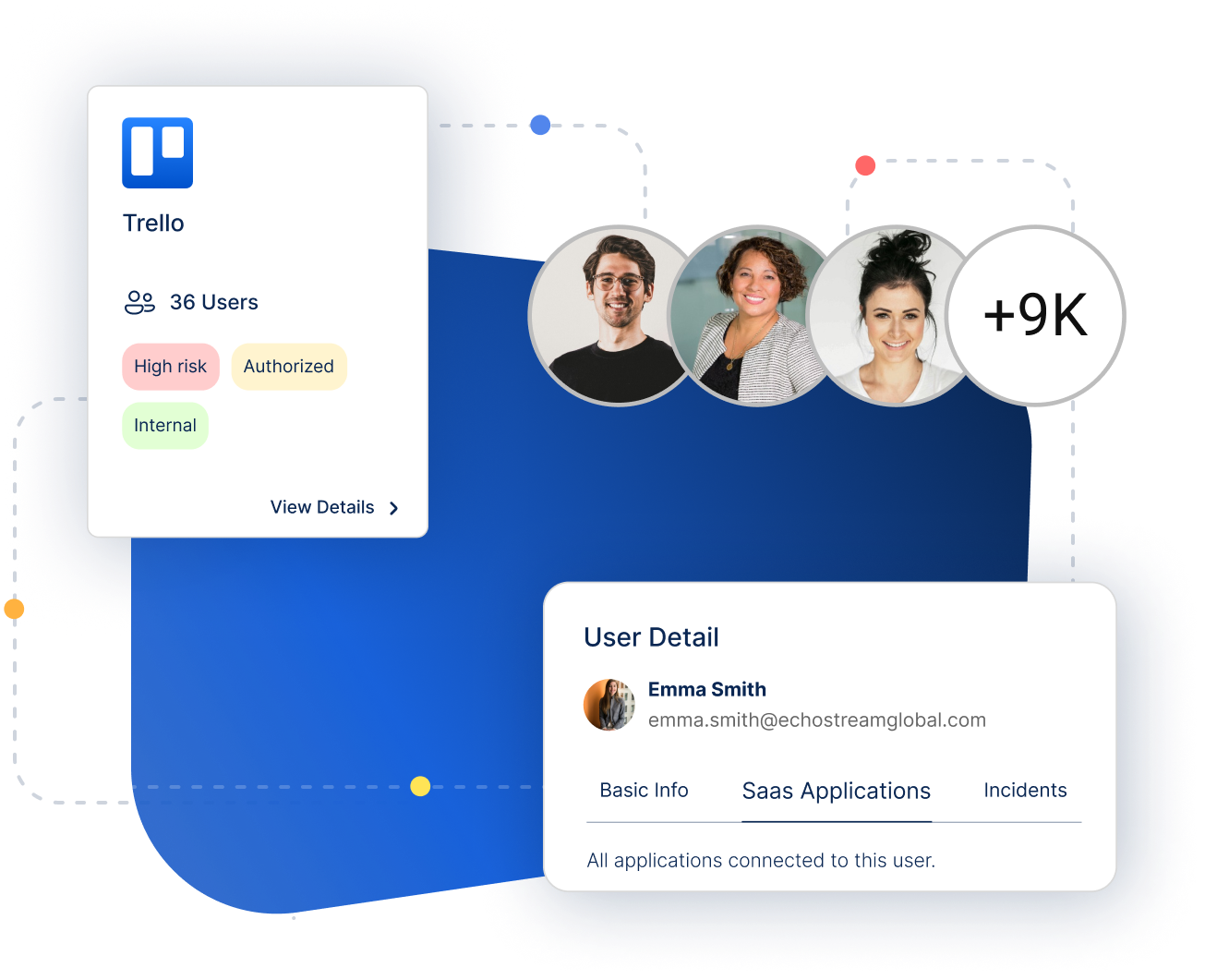
Inadequate control over identity access and authentication methods increases vulnerability to breaches.
Aggregate and analyze user data to detect suspicious activity and mitigate identity-related risks.
Implement dynamic access controls to prevent unauthorized access and respond to threats.
Inadequate control over identity access and authentication methods increases vulnerability to breaches.
Aggregate and analyze user data to detect suspicious activity and mitigate identity-related risks.
Implement dynamic access controls to prevent unauthorized access and respond to threats.

Misconfigurations and non-compliance with industry standards can expose business to risks and regulatory penalties.
Continuously monitor and auto-remediate misconfigurations to ensure compliance with security standards.
Generate detailed reports to demonstrate compliance with industry regulations and best practices.
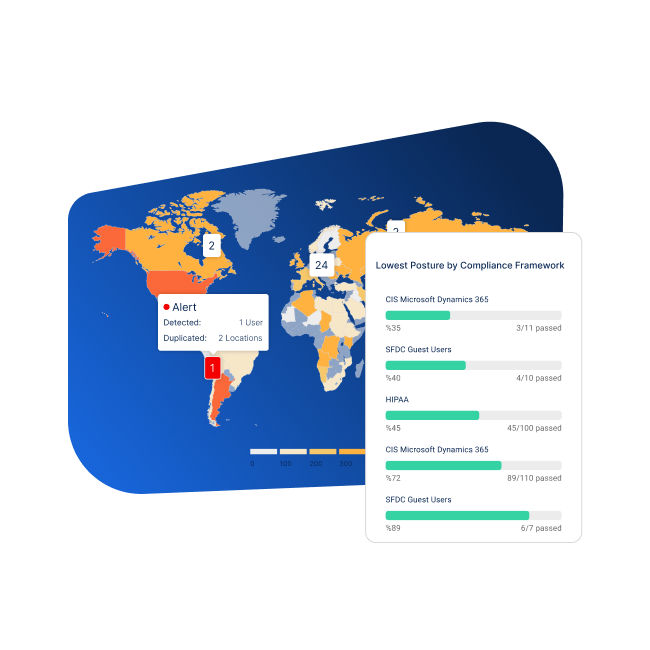
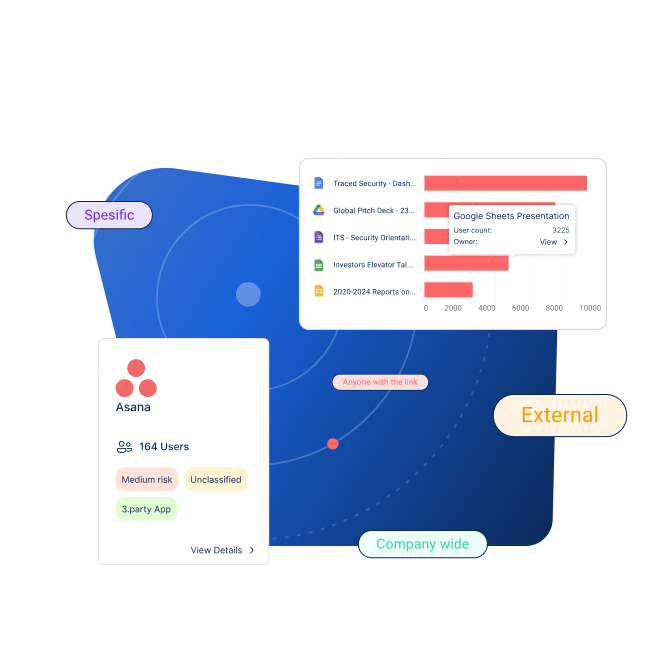
Data breaches and over privileged third party integrations can compromise sensitive information.
Control data access and automate remediation to protect sensitive information from unauthorized access.
Manage and secure third-party integrations, removing inactive or risky connections to minimize exposure.
Data breaches and over privileged third party integrations can compromise sensitive information.
Control data access and automate remediation to protect sensitive information from unauthorized access.
Manage and secure third-party integrations, removing inactive or risky connections to minimize exposure.

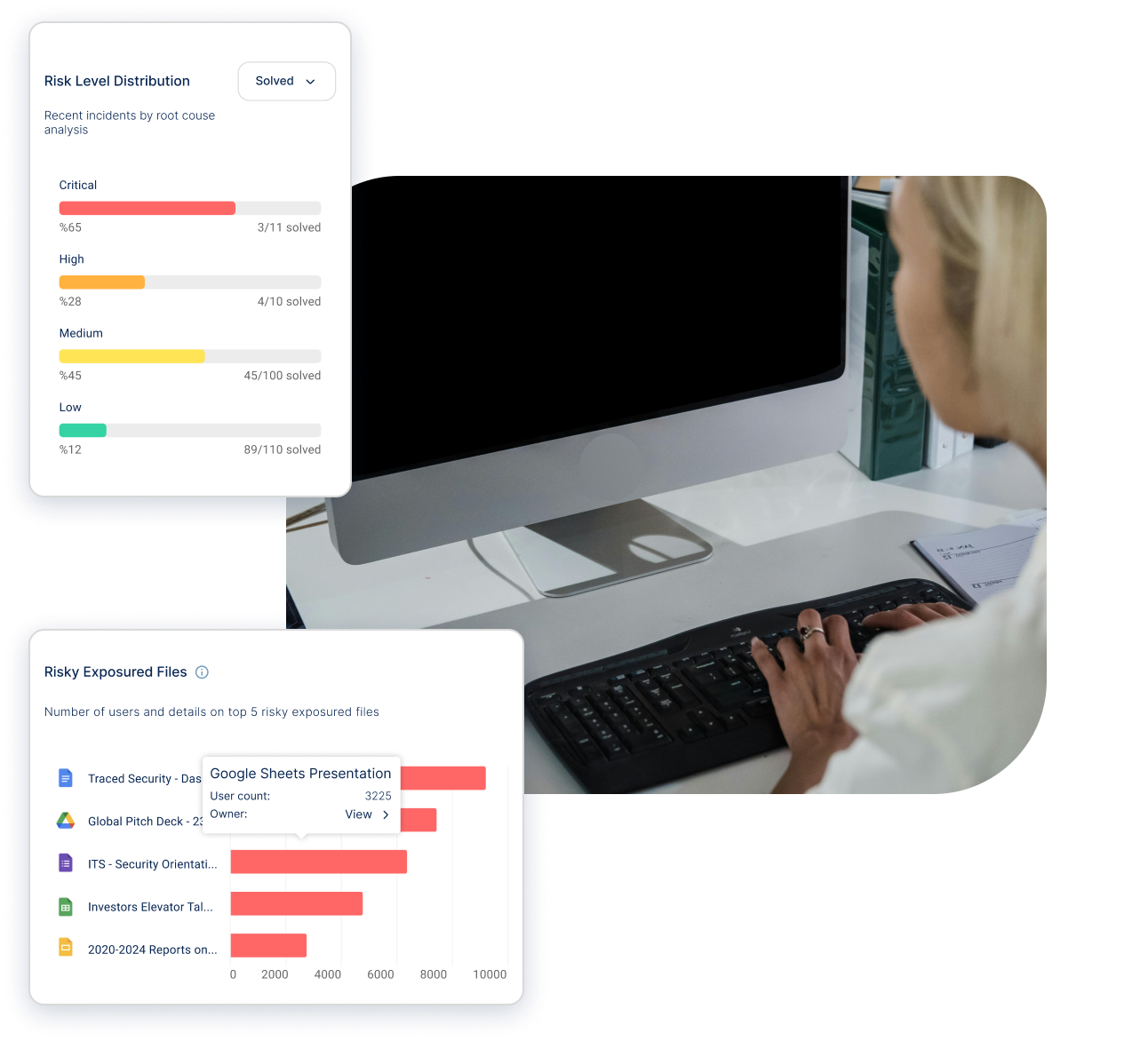
Start by scheduling a demo with our team to see Traced Security in action. Our experts will walk you through the platform and its features.
Our intuitive platform can be set up in minutes, providing immediate insights and security management capabilities.
Once set up, Traced Security continuously monitors your SaaS environment, providing real-time threat detection and compliance management.
What is Traced Security?
Are there any free tutorials available?

Have questions or just want to chat? Reach out—we’re here to help!
46 Camden Road, London, NW1 9DR, United Kingdom