Traced Security Platform
AI-Powered Security for Your SaaS Applications
Gain complete visibility and control over your SaaS applications.
Mitigate risks with proactive threat detection.
Ensure secure and compliant SaaS usage.
Scale security across multiple SaaS applications.
Traced Security Platform
AI-Powered Security for Your SaaS Applications
Gain complete visibility and control over your SaaS applications.
Mitigate risks with proactive threat detection.
Ensure secure and compliant SaaS usage.
Scale security across multiple SaaS applications.

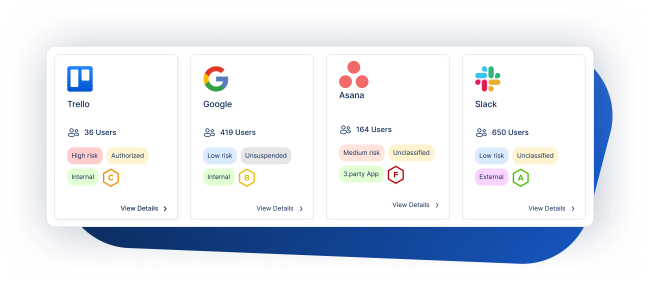
Shadow App Discovery
Manage and secure third-party integrations.
SaaS-to-SaaS Discovery
Effortlessly and consistently identify third-party app access linked to your main SaaS infrastructure.
Understand the Risk Level Permissions
Evaluate the risk levels of permissions granted by users, categorized as low, medium, or high. Detailed descriptions of each permission and clarify what access they entail.
Application Security Score
In partnership with Security Scorecard, we provide clear and concise A-F ratings that cover ten key risk factors, making it easy to assess the security status of your applications.
Automated Remediation
Traced Security offers straightforward auto-remediation options, including revoking tokens, notifying users, or creating service tickets, ensuring prompt action for security issues.
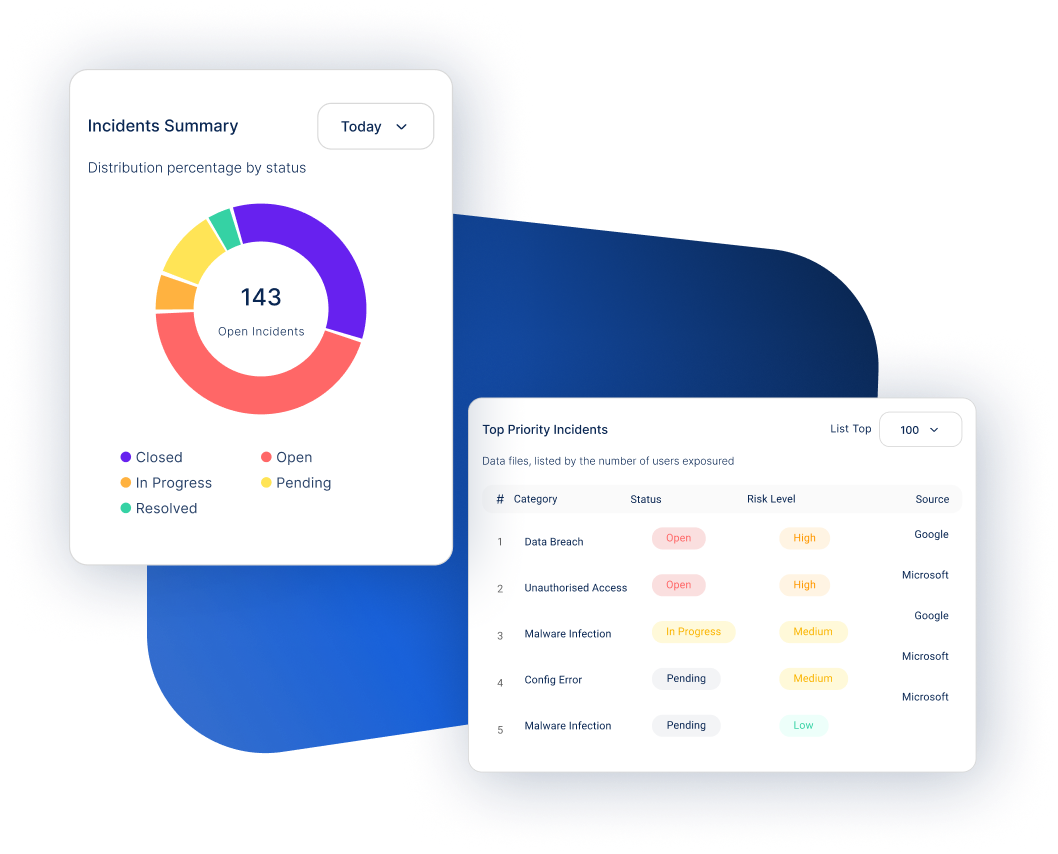
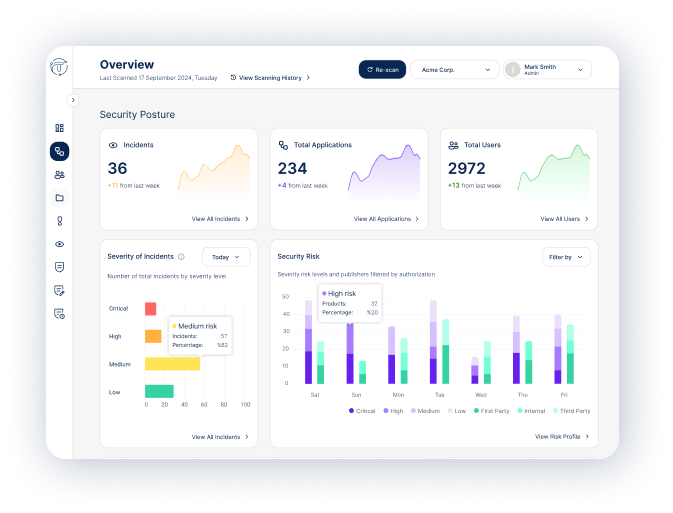
Threat Center
Inadequate control over identity access and authentication methods increases vulnerability to breaches.
Risk Identification
Automatically detect vulnerabilities and potential threats in your SaaS environment.
Threat Assessment
Evaluate the severity of detected risks and prioritize them based on potential impact.
Threat Center
Inadequate control over identity access and authentication methods increases vulnerability to breaches.
Risk Identification
Automatically detect vulnerabilities and potential threats in your SaaS environment.
Threat Assessment
Evaluate the severity of detected risks and prioritize them based on potential impact.

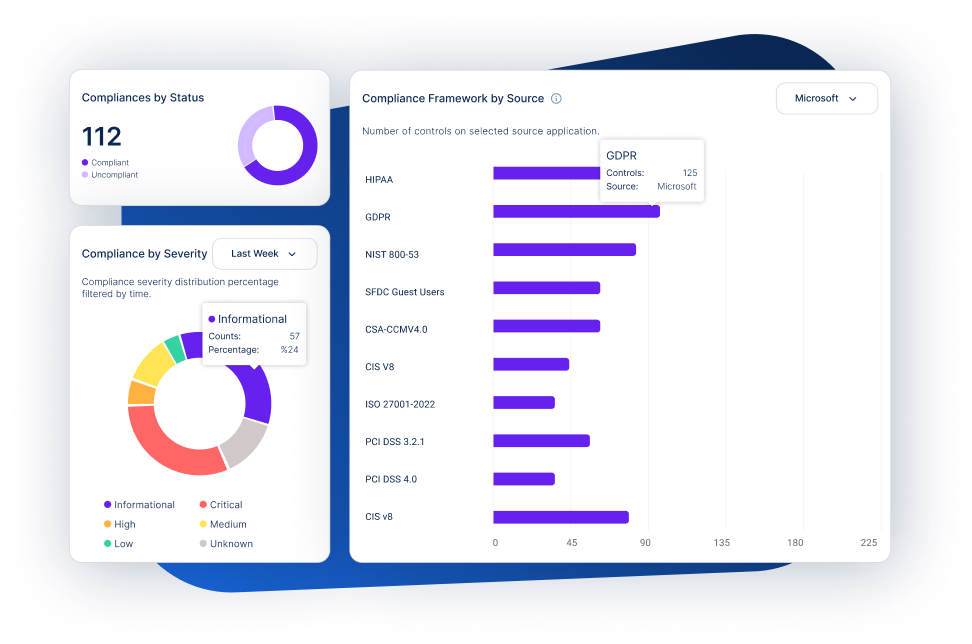
Ensuring Compliance and Security Configurations
Misconfigurations and non-compliance with industry standards can expose businesses to risks and regulatory penalties.
SaaS Misconfiguration Management
Continuously monitor and auto-remediate misconfigurations to ensure compliance with security standards.
Compliance Reporting
Generate detailed reports to demonstrate compliance with industry regulations and best practices.