SaaS Threat Exposure Management
As businesses increasingly rely on SaaS to power their workforce, maintaining visibility into your entire SaaS ecosystem is crucial. Unmanaged SaaS applications can introduce misconfigurations, data exposures, and improper permissions that leave your organization vulnerable to attacks.
Visibility
Comprehensive Visibility
Uncover hidden misconfigurations across your SaaS environment, ensuring no vulnerability goes unnoticed.
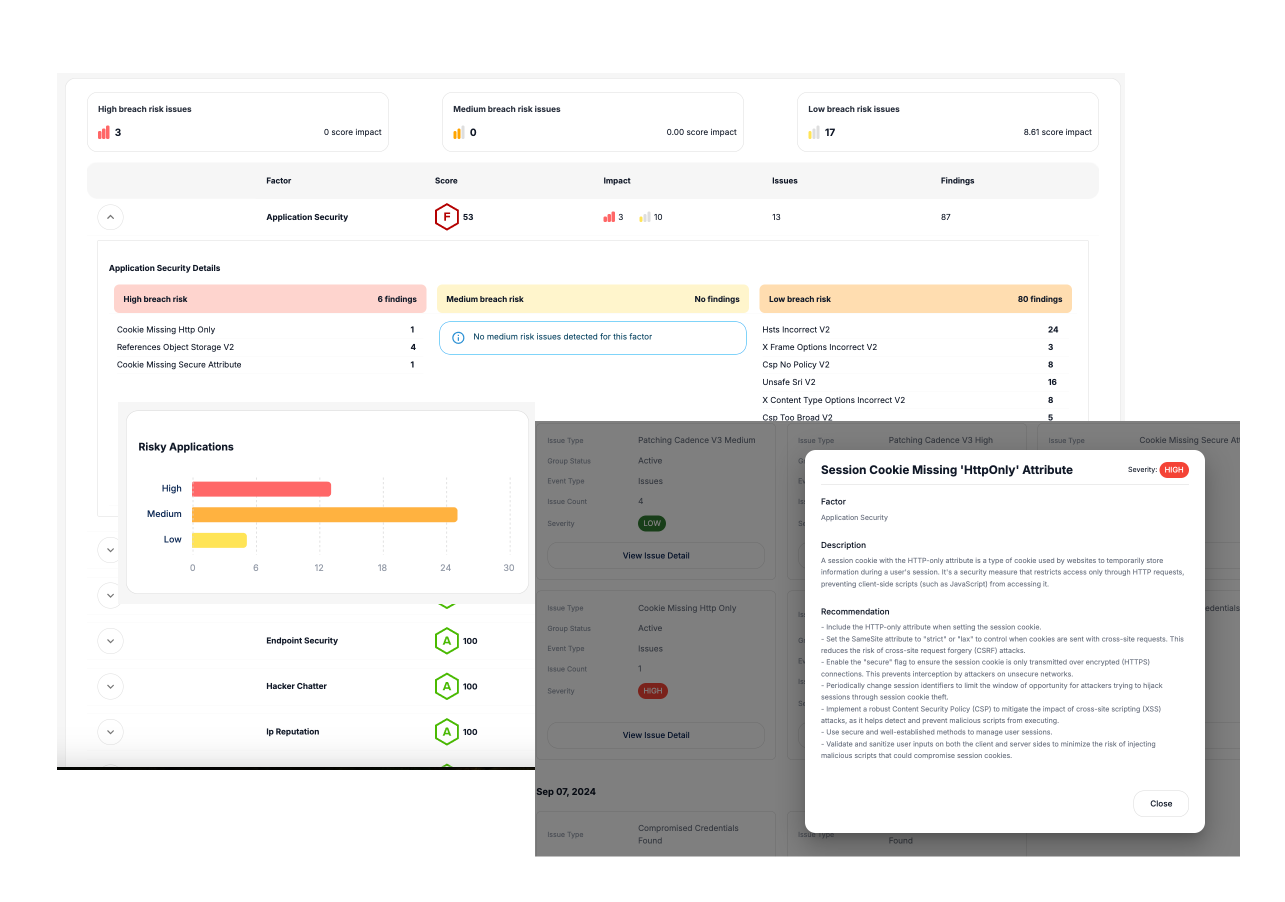
Assess and Remediate Misconfigurations
Continuously scan all SaaS applications for misconfigurations and vulnerabilities, allowing you to take immediate corrective action and enhance the security posture of each app.
Detailed Breach Risk Insights
Understand the potential risks associated with each misconfiguration, including detailed assessments of how they could lead to breaches or data exposure, helping you prioritize and address high-risk issues first.
User Education and License Optimization
Educate users on best practices for using SaaS applications securely, while reducing shadow IT by discouraging the use of unauthorized apps. Additionally, optimize costs by identifying and reclaiming unused licenses, ensuring resources are efficiently utilized.
Visibility
Comprehensive Visibility
Uncover hidden misconfigurations across your SaaS environment, ensuring no vulnerability goes unnoticed.
Assess and Remediate Misconfigurations
Continuously scan all SaaS applications for misconfigurations and vulnerabilities, allowing you to take immediate corrective action and enhance the security posture of each app.
Detailed Breach Risk Insights
Understand the potential risks associated with each misconfiguration, including detailed assessments of how they could lead to breaches or data exposure, helping you prioritize and address high-risk issues first.
User Education and License Optimization
Educate users on best practices for using SaaS applications securely, while reducing shadow IT by discouraging the use of unauthorized apps. Additionally, optimize costs by identifying and reclaiming unused licenses, ensuring resources are efficiently utilized.

securing the data
Data Exposure Prevention
Secure sensitive data by identifying and mitigating improper access or permissions that could lead to unauthorized exposure.
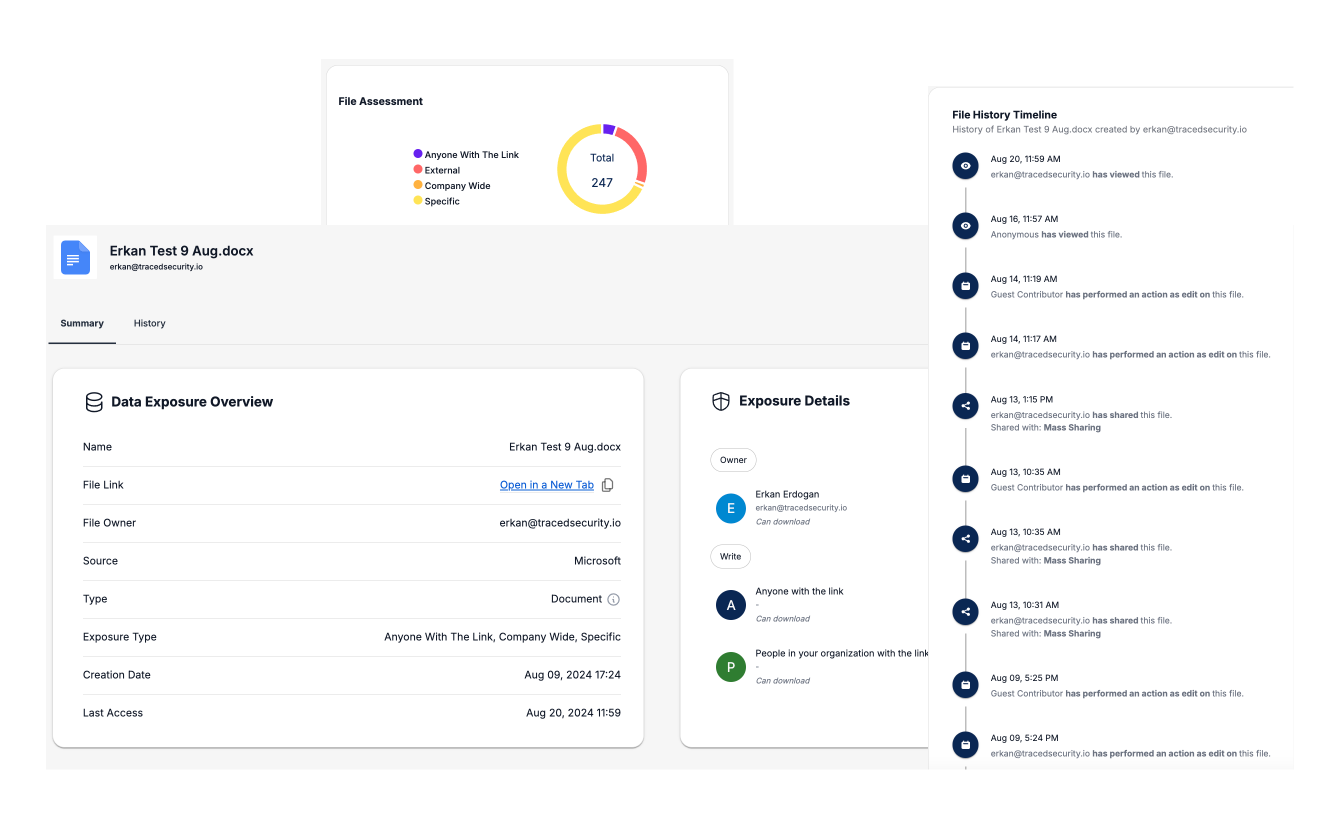
Assess Exposure Risk
Quickly identify how your data has been exposed, whether internally within the organization or externally to unauthorized users, such as through public links or misconfigured sharing settings.
Detailed Exposure Visibility
Gain in-depth visibility into each data exposure, including a complete history of the file—who accessed it, who edited it, and any changes made over time—so you can understand the full context of the risk.
Automated Remediation
Resolve exposures instantly by revoking access or sharing permissions with a single click. Educate users with automated notifications to prevent future risks or create service tickets for review and further action.
SaaS Risk Assessment
Modern organizations are increasingly reliant on SaaS applications, but with this growth comes an evolving and complex threat landscape.
Risk Management
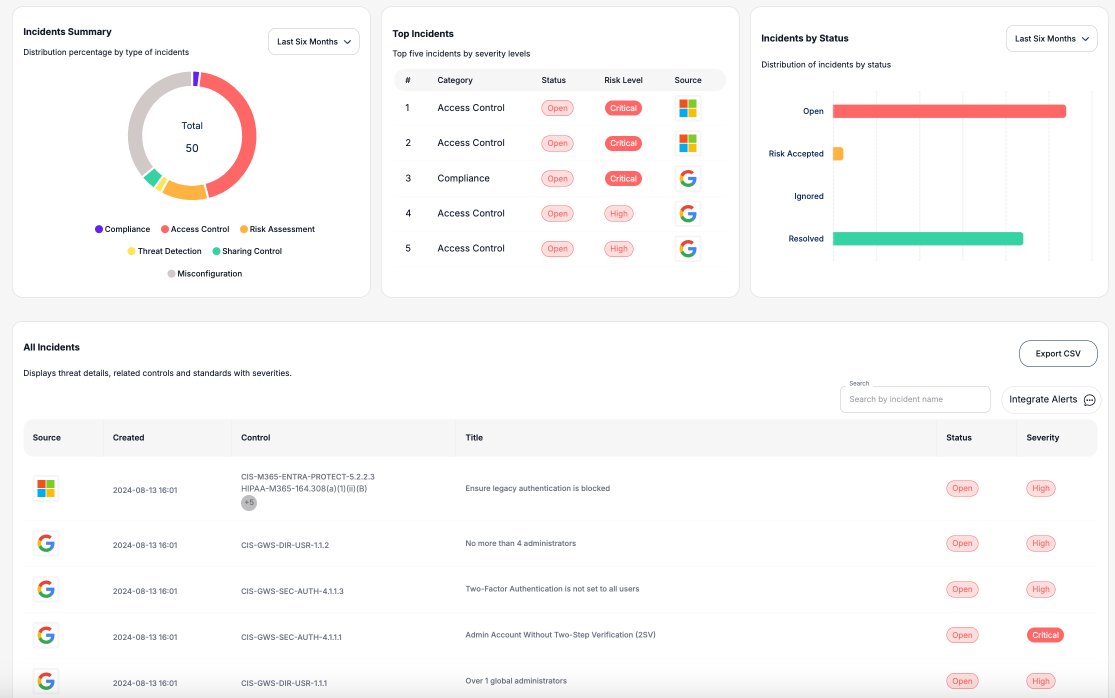
Prioritize Threats
Streamline your security efforts with Traced Security’s intelligent risk prioritization, designed to manage high volumes of findings across your SaaS ecosystem efficiently.
Security Benchmark Mapping
Every finding is linked to industry-leading security benchmarks, such as CIS or NIST, helping you stay compliant and implement best practices.
Clear Risk Indicators
Easily understand each identified risk with comprehensive details, including the severity, affected SaaS components, and business impact.
Risk Management
Prioritize Threats
Streamline your security efforts with Traced Security’s intelligent risk prioritization, designed to manage high volumes of findings across your SaaS ecosystem efficiently.
Security Benchmark Mapping
Every finding is linked to industry-leading security benchmarks, such as CIS or NIST, helping you stay compliant and implement best practices.
Clear Risk Indicators
Easily understand each identified risk with comprehensive details, including the severity, affected SaaS components, and business impact.

Incident Management
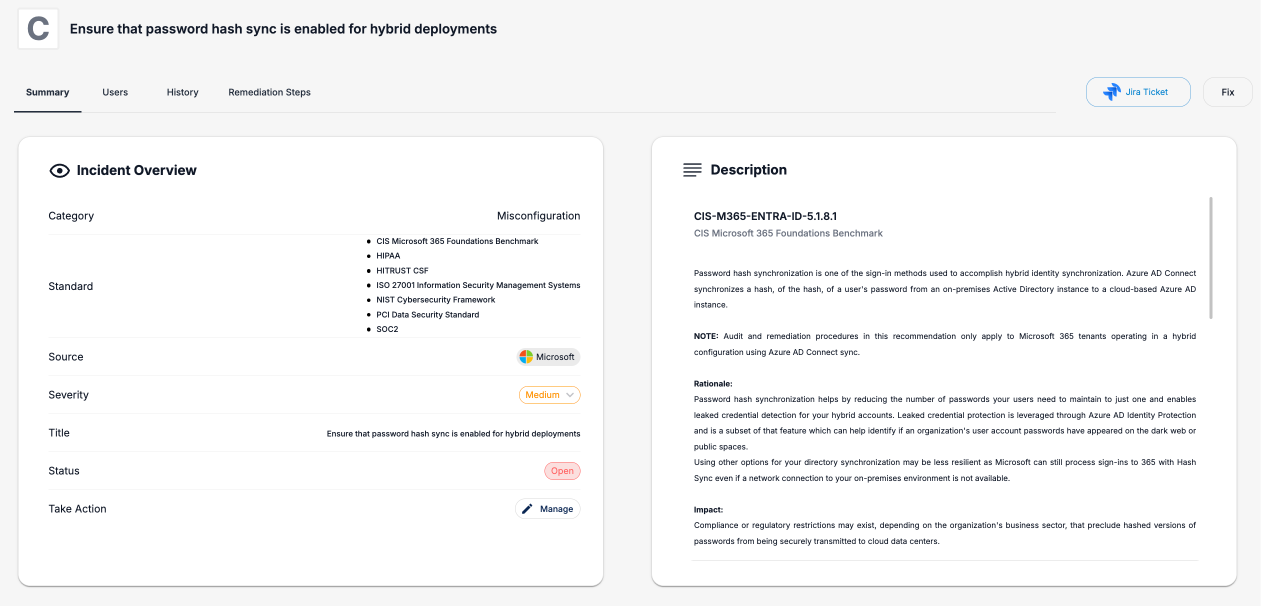
Incident Response and Remediation
Our platform ensures that every security incident is detected, assessed, and resolved efficiently, reducing downtime and minimizing potential damage to your organization.
Actionable Incident Insights
Gain detailed visibility into each incident, including its root cause, affected components, and recommended remediation steps.
Automated Remediation Workflows
Streamline response efforts with automation, allowing your team to resolve incidents faster and with fewer manual interventions.
SaaS Zero Trust
Traditional perimeter-based security is no longer sufficient in today’s cloud-first world, where SaaS applications are widely used and accessed from anywhere. Traced Security implements a Zero Trust model for SaaS applications, ensuring that no user or device is trusted by default—whether inside or outside the network.

Continuous Authentication and Verification
Ensure that every user, and connection is authenticated and authorized before accessing SaaS applications, regardless of their location or network.

Least Privilege Access
Apply strict, role-based access controls (RBAC) to ensure users only have the minimum access required to perform their tasks, minimizing the risk of unauthorized access or data breaches.

Continuous Monitoring and Risk Assessment
Monitor all activity within your SaaS ecosystem in real-time, identifying suspicious behavior, unauthorized access attempts, and potential risks, and responding instantly to mitigate threats.
- of Organizations Experienced a SaaS Data Breach in 2024!31%
- The Number of SaaS Applications Used by Average Enterprise.130
SaaS Data Breach
31% of organizations experienced a SaaS data breach in 2024, a 5% increase over the previous year. This may be linked to inadequate visibility of the apps being deployed, including 3rd party connections to SaaS.
Increase in SaaS Adoption
The average enterprise uses 130 different SaaS applications today, up from 80 in 2020. Gartner predicted that 45% of organizations globally will have experienced attacks on their software supply chains by 2025.

Contact Us
Have questions or just want to chat? Reach out—we’re here to help!
Location
46 Camden Road, NW1 9DR, London, United Kingdom
Email
[email protected]